%20small-1060x400.png)
Continuing last month’s theme of comparing different platforms, in this post we’re looking at security. First, it’s important to understand the main security risks in online store platforms.
The most common security risks in e-commerce platforms
1. Outdated system and plugins
Risk: Using outdated versions of the platform, plugins, or server software contains known vulnerabilities (SQL injection, XSS, RCE).
Prevention: Regularly update the platform, plugins, and server software.
Impact if not fixed: Attackers can take over the store and steal customer and payment data.
2. Weak passwords and insufficient authentication
Risk: Administrator or customer accounts are hacked using brute-force (a cryptanalytic attack where the attacker tries to guess the correct passwords) or credential stuffing (a type of cyberattack that steals user data en masse—passwords and emails—which are then used to log into other systems).
Prevention: Strong passwords, two-factor authentication (2FA), login attempt rate-limiting.
Impact: Unauthorized access to the system, loss of store control, data leakage.
3. Insecure plugins and modules
Risk: Third-party extensions often contain vulnerabilities or malicious code.
Prevention: Use plugins only from trusted developers; where possible, review and audit the code (this requires programming skills).
Impact: Backdoor (a hidden method implemented to bypass normal device/application/system authentication and encryption) insertion into the system, malicious code injection, data leakage.
4. Brute-force and DoS (denial-of-service) attacks
Risk: Automated attacks can lock up the store or crack accounts.
Prevention: WAF (Web Application Firewall), login attempt throttling, a CDN with DoS protection.
Impact: Store downtime—lost revenue and customer trust.
5. Insufficient server security
Risk: Misconfigured hosting (open ports, weak settings).
Prevention: Secure hosting, firewall, regular server audits.
Impact: Attackers gain direct access to the database or file system, leading to a full store compromise.
6. Payment data security gaps
Risk: Leakage of card and other payment data (PCI-DSS non-compliance).
Prevention: Use trusted payment gateways (Swedbank, SEB, Stripe, PayPal), SSL/TLS certificates; don’t store card data on your server.
Impact: Theft of financial data, reputational damage, legal consequences (e.g., GDPR, PCI-DSS fines).
7. Social engineering and phishing
Risk: Admins or customers are tricked into revealing passwords via email or malicious links.
Prevention: Staff and customer education, email filtering, 2FA.
Impact: Unauthorized system access, account takeovers, data theft.
8. Insufficient data encryption and backups
Risk: Data is intercepted or lost due to an attack or system failure.
Prevention: HTTPS site-wide, database encryption, regular off-site backups.
Impact: Data leakage, business continuity risk, inability to recover after a cyberattack.
After reviewing the common risks above, you can see that not all security questions depend solely on the platform used—plugins, server configuration, and clicking weird links on the internet or in your inbox also matter.
To understand which e-commerce platform is the most secure, you need to look at the specific technologies and solutions that are built into the platform and whether they can be installed without interfering with the code.
Protection against XSS attacks
Cross-site scripting (XSS) is a security vulnerability that most often affects web applications. It allows someone to inject malicious code (usually JavaScript) into the storefront. It doesn’t directly affect the site/store itself, but the end user visiting it. It can cause malicious outcomes such as stealing session cookies, impersonating the user, performing unauthorized actions on the user’s behalf, and accessing confidential data.
Let’s see how four popular platforms handle this.
OpenCart 4 – very good!
OpenCart 4 uses the Twig templating system, which automatically escapes output. In plain terms: if someone tries to “insert” unwanted code into a form or comment, the system converts it into harmless text.
It’s also worth setting CSP headers on the server—thanks to them, the store tells the browser where it can and cannot load scripts from. In practice, it’s like a shield saying, “Hey, don’t do anything I haven’t approved!”
Rating: 4/5. Default protection + the ability to harden further without major changes.
Magento (Adobe Commerce) – strong protection, but…
Magento has robust built-in mechanisms: all user data is validated and “sanitized” before rendering. It uses functions like escapeHtml to do this.
But there’s a catch… a lot depends on extensions. If you add a module that doesn’t follow Magento’s security rules, XSS can slip in despite the strong core. [1] Adobe (Magento’s owner) does a lot to control this, but not everything can be predicted.
Rating: 4/5. Solid in theory, but you must be careful with what you install.
PrestaShop – caution advised here
PrestaShop does not offer as strong protection by default. Security mainly depends on updating the system and using additional tools (like a WAF or security headers).
History shows XSS is quite common in PrestaShop. There have been cases (e.g., CVE-2024-34716, PrestaShop 8.1.0–8.1.5) where such a flaw could even allow remote takeover of the store. [2] These bugs get fixed, of course, but if you don’t apply updates, risk remains high.
Rating: 3/5. Requires extra work and constant updates. For non-technical users, it can be too risky.
WooCommerce – depends on what you install…
WooCommerce, as a WordPress extension, leverages its security mechanisms—and they’re fairly sensible. WP provides functions like esc_html(), esc_url(), and wp_kses() to ensure malicious JavaScript isn’t injected into the page.
It’s a bit like checking your groceries at the checkout—everything that enters the site gets filtered, and unwanted code is rejected.
The problem starts when you install a plugin from an unknown source or one that’s two years out of date. And that’s not just theory. According to a 2024 report, 96% of WordPress security issues are caused by plugins. [3]
So WooCommerce can be secure, but it largely depends on you: regular updates, thoughtful plugin/theme choices. Also set security headers (like Content-Security-Policy) to strengthen XSS defenses.
Rating: 2/5. You can protect yourself, but it requires understanding and a systematic approach. Beginners can easily miss something.
Protection against CSRF attacks
CSRF (Cross-Site Request Forgery) is another attack that can cause major headaches for store owners. In short: someone pretends to be a logged-in user and performs actions on their behalf that they themselves did not plan to perform —like changing a shipping address, canceling an order, or, in the admin’s case, deleting products or changing a password.
Let’s see how popular platforms handle this:
Magento – secure, but…
Magento uses “form keys”—unique “stamps” appended to forms and requests. The server checks whether the key matches the current session—if not, the request is rejected. Simple and effective.
But note: technically, Magento allows bypassing this protection, e.g., in custom integrations. Problems often arise here—someone writes a plugin that sidesteps security and CSRF slips through. [4] So in Magento, much depends on the developer.
Rating: 4/5. Well-protected unless someone intentionally weakens it.
PrestaShop – once weak, now better, but risks remain
PrestaShop uses security tokens (codes that help verify legitimate access). In the past, there were many issues—for example, in 2023 a vulnerability [5] allowed reusing old session tokens to access the admin panel. In other words—once you’d gotten in, you could continue getting in when you shouldn’t. This bug was fixed, but some distrust remains.
Even now, users often encounter “CSRF token invalid.” That means the token isn’t recognized and access is denied. The issue appears inconsistently—more often with specific modules or certain hosting providers. Unfortunately, some store owners choose to disable the protection entirely rather than fix the underlying problem, reducing security.
Rating: 3/5. The system works, but it’s fragile—easy to break or disable an important control. Handle with care.
OpenCart 4 – lightweight protection, but in the right direction
OpenCart uses tokens appended in the URL (e.g., user_token). You can view this as a kind of session signature confirming the request is from the real user. This approach is mainly used in the admin panel to protect against baseline attacks.
However: comprehensive, unified protection isn’t present everywhere—e.g., on the customer side. Admin actions are largely protected, but if the store is extensive with many features, we recommend adding extra security layers yourself.
Rating: 4/5. Works for everyday use, but not perfectly comprehensive.
WooCommerce – great tools, but it’s up to you
WooCommerce relies on WordPress nonces—one-time codes assigned to a specific user action. They can be added to forms, buttons, or even links. A very useful mechanism that protects well if used correctly.
But again—plugins. This excellent protection is only as strong as the people using it. Over 90% of WordPress security problems come from plugins, so it’s not hard to guess where the weak point is. If plugins are low quality or not updated regularly, protection becomes fragile.
Rating: 3/5. The mechanism itself is excellent, but security largely depends on plugin quality and maintenance.
Protection against SQL injection
SQL injection exploits system weaknesses. It’s still one of the most common intrusion methods. An attacker who knows about a vulnerability can insert commands (SQL code) where they don’t belong and gain access to the store’s database.
The result? The attacker can access the database—which holds everything that shouldn’t fall into the wrong hands: customer data, orders, passwords, and lots of other sensitive info.
SQL injection is considered one of the most dangerous attacks—it’s like opening the door from the inside if security isn’t set up properly.
Magento – strong SQLi protection, with one “but”
Magento’s SQL protection is high-level. It uses prepared statements—a safe way to pass data in SQL queries. In simple terms, data and commands are sent separately, so user-provided input can’t accidentally (or maliciously) change the intent of the query.
Additionally, Magento uses its own ORM (a “translator” between PHP code and the database) that automatically makes queries safer.
However, there’s a key risk: many SQL attacks in Magento environments occur through poorly written plugins or custom modifications. [6] In other words—the core is very secure, but as soon as you install low-quality extensions, security drops.
Rating: 4/5. Solid base, but be careful with add-ons.
PrestaShop – historical SQLi risks
PrestaShop also uses prepared statements, but not always and not everywhere. There have been serious SQLi vulnerabilities—including ones that allowed theft of payment card data.
There have been cases where a popular module had such a severe vulnerability that a remote attacker could take over the store. [7] And since PrestaShop relies heavily on external modules, the risk is particularly high.
Therefore, in addition to regular updates, a Web Application Firewall (WAF) is recommended to block malicious requests before they reach the store.
Rating: 3/5. Baseline protection exists, but reliance on modules significantly increases risk.
OpenCart 4 – security depends on the developer
OpenCart 4 supports prepared statements, a safer way to pass data to the database. But unlike some platforms, OpenCart doesn’t enforce using an ORM—this means more freedom for developers, but also more risk. With an experienced developer, the system is secure. With a beginner or careless coder, security holes can appear.
On the positive side, OpenCart 4’s code is much more structured than earlier versions, and the architecture has improved. That helps security. But as usual—third-party extensions are the most common weak point.
Rating: 3/5. Security is achievable, but highly dependent on how—and by whom—the system is built.
WooCommerce – great tools, risky ecosystem
WooCommerce builds on WordPress, where the global $wpdb object and $wpdb->prepare() provide protection. Used properly, they ensure solid defense.
The problem is that many plugins and themes don’t use them—or use them incorrectly. So we circle back to the old problem: a great platform with a risky plugin ecosystem.
It’s also worth using a WAF and conducting code audits—especially for high-traffic stores.
Rating: 2/5. The mechanism is reliable, but security depends on plugin quality and regular maintenance.
Secure password storage – what’s behind the screen?
We’ve covered XSS, CSRF, and SQLi; now it’s time for something that affects every user: passwords.
This isn’t about where the client writes their password (on paper or in the browser), but what the store does with the password on the server side.
Remember: if a store keeps passwords in the database in “plain text,” it’s not a store—it’s a ticking time bomb.
So let’s see which platforms truly hash passwords, which only pretend to, and where store owners can sleep soundly.
Magento
Magento is exemplary for password storage. It uses bcrypt—an algorithm that’s deliberately slow… which is exactly why it’s good. Why? The slower the cracking process, the harder it is even for a supercomputer to guess the password.
Additionally, each password gets a random salt, ensuring even identical passwords look completely different in the database.
You can also enforce sensible password length, digits, uppercase letters, special symbols—everything you need.
Rating: 5/5. Excellent password protection.
Prestashop
This one is more nuanced. Older PrestaShop versions (before 1.7) stored passwords using MD5—today you can crack that with a regular home PC and a decent GPU.
Newer versions have likely moved to bcrypt, but… it’s unclear from which version, how old passwords are migrated, and whether users are safely rehashed upon their next login.
This means that despite improvements, you still need to be cautious—especially if the store was migrated from very old versions.
Rating: 3/5. Progressed, but with risks due to old data.
OpenCart 4
Here we finally see progress. Older versions (1.x, 2.x) used SHA1, which is no longer considered secure. But OpenCart 4 (at least in GitHub) already uses password_hash()—PHP’s built-in function that defaults to bcrypt.
So if your store runs on a clean OpenCart 4, evidence suggests passwords are stored properly. But if you upgraded from older versions, ensure old passwords get rehashed after the user’s next login. Otherwise, weak, old hashes may remain in the database.
Rating: 4/5. Secure in the new version, but watch the migration path.
Woocommerce
WooCommerce inherits WordPress’s password system—secure for a long time thanks to PHPass.
The best news: WordPress 6.8 introduces a new, even more secure system based on bcrypt + SHA-384. This makes password cracking even harder. Passwords are automatically upgraded to the new standard on the first login after updating.
That’s excellent work and proof the ecosystem is advancing security-wise.
Rating: 5/5. Secure system with a clear roadmap.
Changing the default admin path – a simple way to boost security
You know that feeling when you try to open a door, but the key isn’t where you expected? That’s how custom admin URLs work.
This is “security through obscurity.” It doesn’t replace strong passwords or brute-force protection, but it does something useful—makes it harder for bots to reach the admin side.
Here’s how it looks across platforms.
Magento
Magento fully supports a custom admin URL. Instead of the default /admin, you can set something less obvious, e.g., /panel-shop-87.
What’s more—Magento can add secret keys to URL links, which means even if someone knows the path, they won’t get in without the key. Smart!
You can change the path in the admin panel or in env.php.
Rating: 5/5.
Prestashop
PrestaShop allows this too. Simply rename the admin folder on the server, e.g., zumparizum987. Quick, simple, and it works.
The platform recognizes the new name and offers to log in via the new path. No magic, but bots scanning for /admin won’t get in.
Just be careful not to overwrite the custom folder during updates.
Rating: 4/5.
OpenCart 4
OpenCart earns extra points here.
Yes, you can also rename the admin folder (e.g., vishum2025) and then just adjust paths in config.php and admin/config.php. So—like PrestaShop: quick, manual, but effective.
More importantly—by default, OpenCart 4 moves the storage directory outside the public web root. That means temp data, backups, or log files aren’t in a location visible to everyone but in a safer zone. A very smart step that reduces risk if someone “peeks” at your folder structure.
Rating: 5/5.
Woocommerce
WooCommerce runs on WordPress, and admin access is always via /wp-admin or /wp-login.php. You can’t change the default path without extra plugins like WPS Hide Login.
These plugins work, but they’re still plugins—they can be outdated, cause conflicts, or, worst-case, contain vulnerabilities. In practice this works, but requires greater vigilance.
Rating: 1/5. Can’t change the path without a plugin. With a plugin—you can, but risks increase.
Separation of extension files and modularity — what does it mean?
Before diving into technicalities, let’s explain it plainly. Online stores, like any software, grow over time: you add features, integrations, payment methods, sliders, and more. How do you do that without breaking the store during updates and without creating code chaos?
Modularity means building the store so new features can be installed as separate “blocks” (modules) without touching the system’s “heart.” This allows you to:
- update the store more easily,
- keep the code tidy,
- reduce the risk that one change breaks the whole system.
Here’s how popular platforms handle it:
Magento
Magento is like e-commerce LEGO, and in terms of modularity it’s textbook. Each extension has its own folder, e.g., app/code/MyStore/ModuleName, which keeps things tidy.
Code is layered—business logic is separated from views and the database. It’s like separating the kitchen, dining room, and dishwasher—each does its job.
Pros:
- Very good separation of concerns,
- Organized structure,
- Easier to isolate bugs.
Con:
- The system is complex—not every developer can grasp it without experience.
Rating: 5/5. Excellent modularity but demands experienced developers.
Prestashop
PrestaShop is also module-based—each module has its structure and is separated. Since 1.7, the platform uses Symfony and Twig. That means a more professional architecture, clearer separation, and greater capabilities.
Pros:
- Modules don’t touch the core,
- Easier updates,
- Modern architecture (Symfony, Twig).
Con:
- Older versions were significantly weaker here.
Rating: 4/5. Newer versions are much better, but heritage from old solutions can still be a problem.
OpenCart 4
OpenCart 4 has made a big qualitative leap in architecture and code organization. It still follows MVCL (Model–View–Controller–Language) but now clearly separates system and external files.
What does this mean?
Extensions, themes, modules, and integrations no longer mix with system files—everything goes under the extension/ directory.
Advantages:
- Core updates don’t overwrite extensions,
- Clear what’s system vs. custom,
- Tidier and easier to debug.
Extras:
- Twig template engine improves security (e.g., auto-escaping),
- An event system lets you change behavior without touching core code,
- The classic admin/ and catalog/ split remains for each plugin.
Rating: 5/5. The most organized OpenCart version to date.
Woocommerce
WooCommerce is a WordPress plugin, and extensions are additional plugins. Each has its own folder, code, and style. WordPress encourages some structure (includes/, assets/, templates/), but nothing stops a developer from making a mess.
Pros:
- Very flexible,
- Many add-ons available.
Cons:
- Plugin quality varies widely,
- Limited system control—if a plugin is poorly built, quality won’t be there.
Rating: 4/5. Flexibility is a plus, but plugin quality and limited control pose risks.
Security scoreboard for online stores – time for the overview!
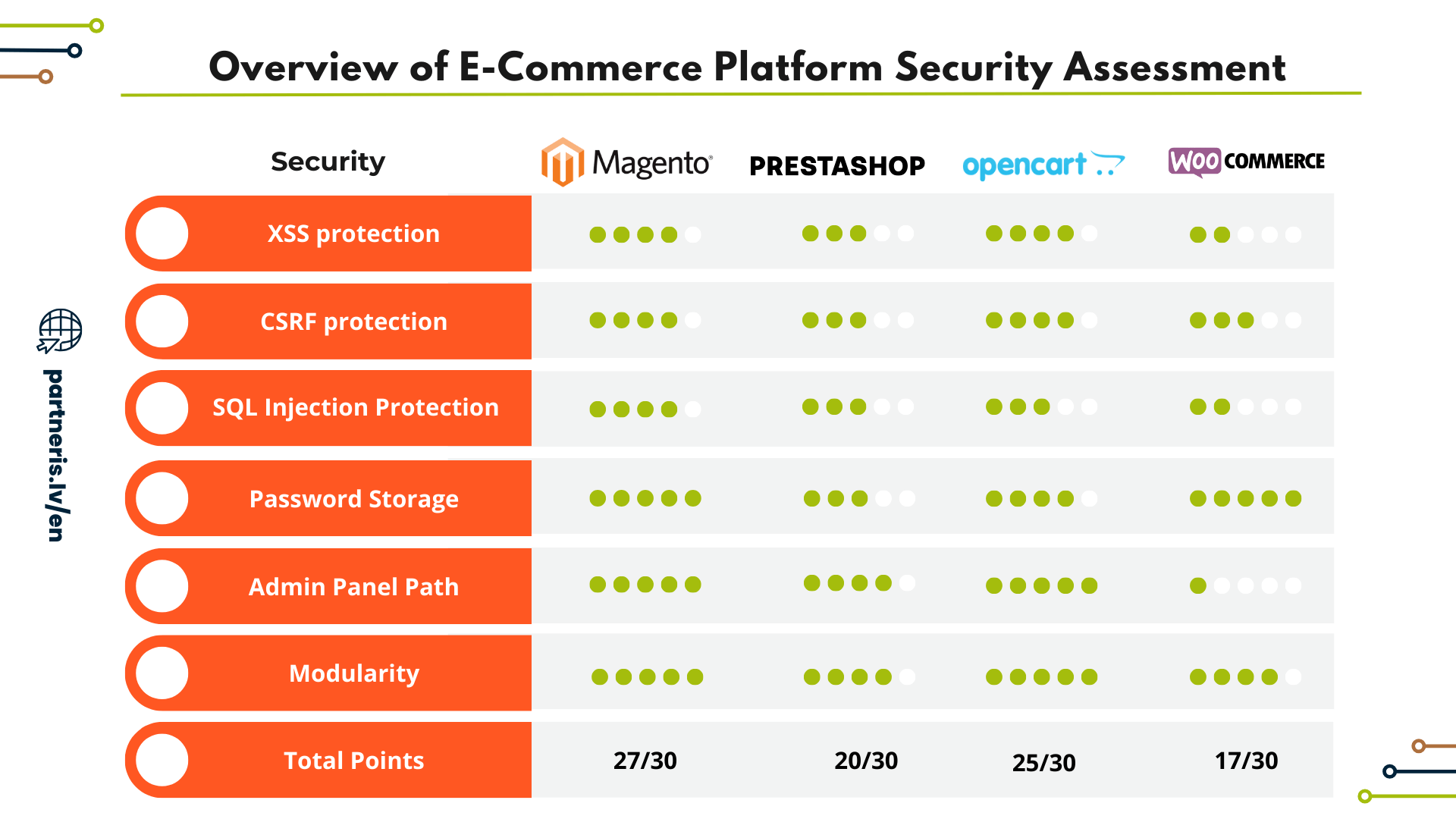

Leave a Comment